Impero Solutions
ContentKeeper
Web Filtering and Security Platform for Schools. Unmatched Cross-Platform Protection in the Cloud.
Real-time protection
The internet is a valuable resource for educational content, but it can also be harmful to student’s safety and wellbeing. Impero’s intelligent web filtering provides multiple layers of cross-platform intelligence that enable safety and security benefits, including real-time visibility, control of non-managed devices, filter circumvention and ransomware defense.
Safe Online Learning
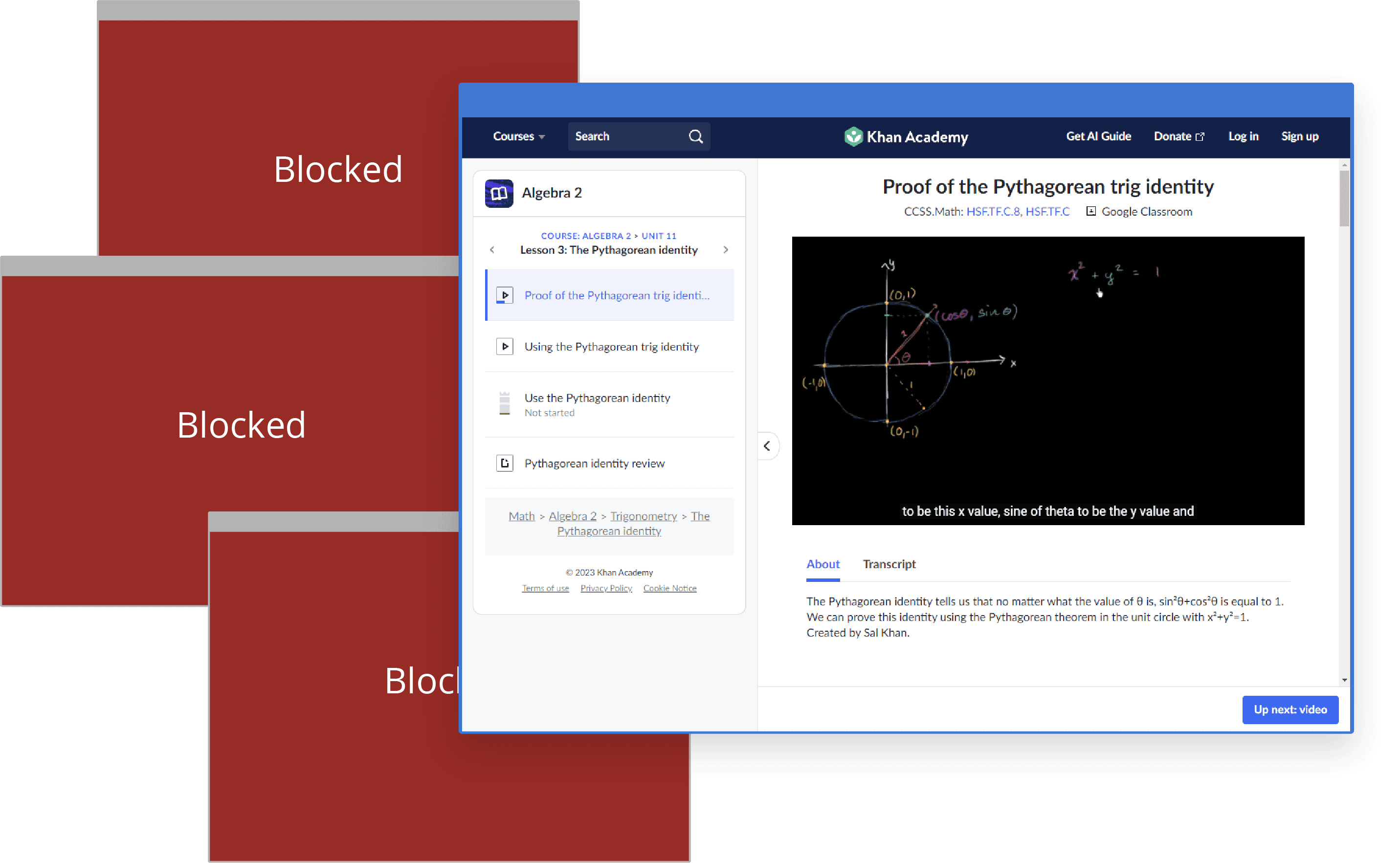
Our web filter for schools uses AI categorisation to analyse web traffic and automatically block web content containing pornography, substance abuse, extremism and other categories of sensitive and potentially harmful material. Blocks zero-day malware, viruses and direct IP URLs for additional security.
Reliable SSL inspection and granular domain controls eliminate over-blocking, so schools can provide safe access to popular domains including Vimeo, Google and YouTube that add value to learning.

Protect Students anywhere
Impero’s web filtering solution for schools uses a combination of device-based agents, cloud services, or on-premises hardware to protect students on any device, regardless of their location. Seamless integration with popular directory services, including Microsoft Active Directory, Apple Open Directory, and Google Workspace, ensures age-appropriate policy management and accurate reporting.
Deeper Insights for Smarter Action
IT administrators know that if you can’t measure it – it doesn’t matter. But it’s challenging to monitor, manage, secure and report on all web activity, particularly with today’s hybrid learning environment. Impero's reporting solution makes it easy to monitor web usage and security threats in real-time. So, you can minimize risk, monitor activity, secure your network, and share detailed insights for policy compliance and smarter decision-making.
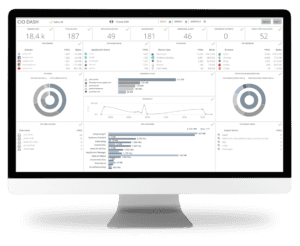
See All Web Activity And Share Results with Ease
Are you ready to get started?
See and Share the Complete Picture

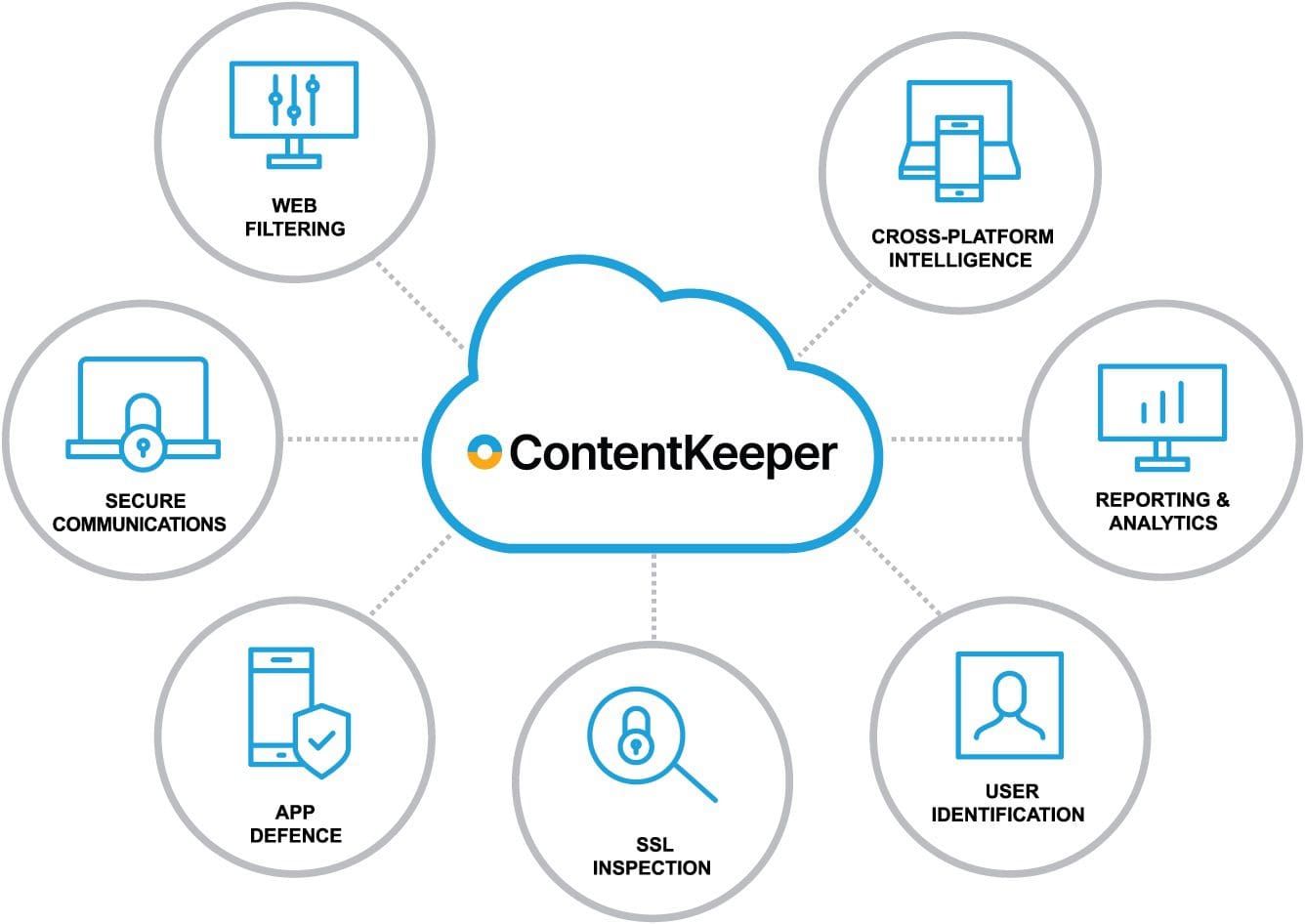
Visibility & Control
Intelligent 360-degree dashboards display who, what, when, and where data is accessed and how it is used on and off campus. Real-time visibility and granular policy-based domain (and sub-domain) controls ensure dangerous activities, rogue apps, ransomware, inappropriate content, and VPN workarounds can be seen and prevented immediately.

Superior Security
ContentKeeper Cloud doubles-down on security, providing intelligence and analytics well beyond traditional Chrome-dependent cloud-based filtering solutions with reliable SSL inspection and cross-platform control. Filtering intelligence, AI, and machine learning work together to detect threats and enable safe web access for students without over-blocking access to popular domains.

Cross-Platform Intelligence
ContentKeeper Cloud works across every web browser, device, and platform (iOS, Mac, Windows, Chrome, IoT, BYOD, and more). So, you can ensure safety and security in hybrid learning environments while supporting effective instruction with centralize management of school-issued and student-owned devices.

Flexibility & Scalability
Whether you choose 100% Cloud, Hybrid, or On-Prem, our seamless deployments won’t interrupt operations and provide scalability on demand to expand coverage when and where you need it. Plus, our cloud-based framework lets you filter off-site devices without having to send traffic back to the school’s network.

Real-Time Monitoring & Analytics
See and share everything happening on your network with 360-degree intelligence dashboards, in-depth analytics, real-time monitoring and alerts, and comprehensive forensic-level reporting for policy compliance and a safer, more productive learning environment.

Cut Costs & Complexity
With ContentKeeper Cloud, you can eliminate Capex spend for onsite infrastructure and experience a lower Total Cost of Ownership (TCO) from the start. Granular policy-based controls make it easy to create and maintain safe, policy-compliant environments and identity excessive bandwidth consumption to lower costs and optimize network performance.
Flexible Deployment
Impero’s flexible deployment options provide limitless configuration options using combinations of device-based agents, cloud services or on-premises hardware to meet the needs of ANY customer.

Cloud
Fast and easy to deploy, cloud-hosted filtering scales on demand so schools can expand coverage when needed while minimizing administrative burdens and overhead. Utilizing installed agents on managed devices and cloud-based DNS filtering for non-managed devices, ALL your devices are covered, including BYOD and IoT.

On-Premises
On-premises deployments feature in-line hardware and services for maximum control and security. Agents on your managed devices allow consistent filtering when students use devices at home or off-premise.

Hybrid
Our innovative hybrid deployment provides multiple layers of intelligence that enable the advanced security options of an on-premise deployment with the scalability and easy administration of the cloud.

ContentKeeper Features:
- Multi-platform filtering intelligence
- Age-appropriate policy management
- SSL inspection and granular domain controls
- Filter circumvention and ransomware defence
- Real-time monitoring, analytics and reporting
- Flexible deployment options
+ Add On
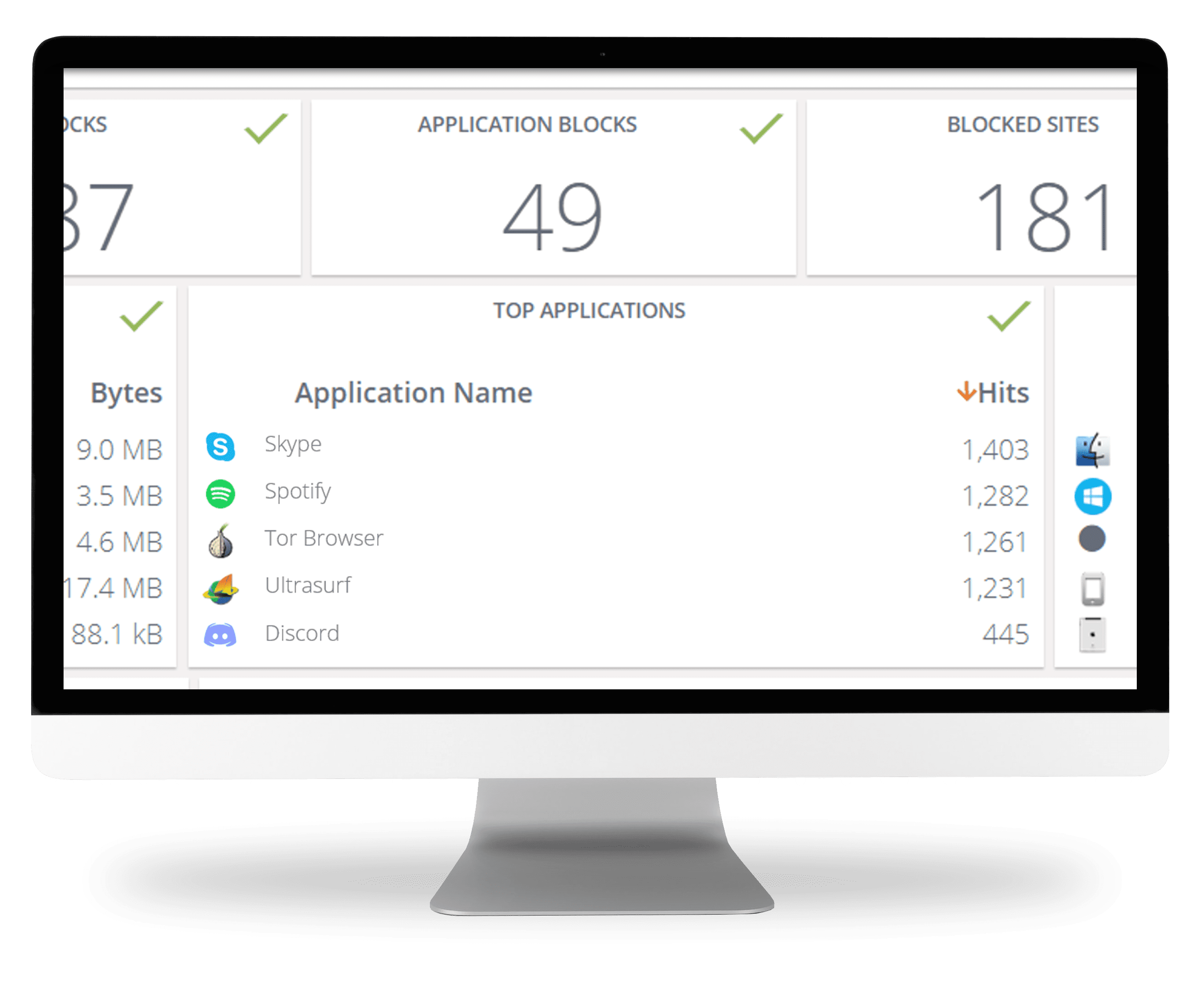
Prevent Prohibited Apps and Protect Your Network
With the shift to remote work, it’s even harder to prevent the use of unwanted applications that circumvent security policies and can undermine compliance. Suspicious and prohibited apps can open a backdoor to malware, eat up bandwidth, and threaten your data, users, and network performance. ContentKeeper’s App Defender makes it easy to identify and block unwanted applications – providing unmatched protection against malware, ensuring policy compliance, and improving security across your entire organization.
Book a Demo
Partner Confidence and Collaboration
As a web security leader for more than two decades, we devote ourselves to protecting the people, digital assets, and networks of businesses, agencies, and organizations across the world. We're just as committed to protecting our partners.
We’re also 100% channel focused. We know you are our front line – and we position you to expand profit margins and capture recurring revenue. You'll have our proven technology, leading-edge security expertise, and powerful reputation in your back pocket for every prospect and customer interaction. Plus, qualified leads along with extensive sales and marketing are always at the ready to help you explore new opportunities and nurture existing customers.



